Database Vulnerability Checklist
 Databases continue to be hacked and confidential personal information continues to be stolen (here’s the latest instance). There is a 28% possibility that yours will be hacked into in the next 12 months (according to the IOUG Data Security Survey).
Databases continue to be hacked and confidential personal information continues to be stolen (here’s the latest instance). There is a 28% possibility that yours will be hacked into in the next 12 months (according to the IOUG Data Security Survey).
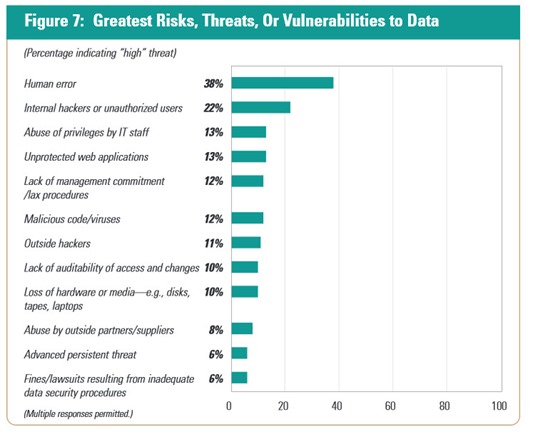
To know where you risk factors lie, examine this chart (from the same survey):
Notice how the top three risks are from “inside jobs”?
Without further ado, set up a bulletproof authentication system with carefully assigned privileges, change authentication details regularly, check your applications for vulnerabilities and GIVE DATABASE SECURITY DUE PRIORITY!!